Email providers such as Gmail and Outlook have built-in spam filters that automatically detect and filter suspicious or potentially malicious emails as spam.
But with about 3.4 billion spam emails being sent each day, one or two emails are bound to slip through the cracks and end up in your inbox.
In this article, we share 5 red flags to help you spot confirmation email scams so you can protect your valuable information and money!
1. Suspicious sender information
If you receive a confirmation email and open it to see what all the hubbub is about, make sure to pay attention to the sender before responding.
Once you open the email, expand the sender’s information to see the email domain.
While the sender’s name might be under a legitimate company, the email address in phishing emails will be slightly misspelled or completely unrelated.
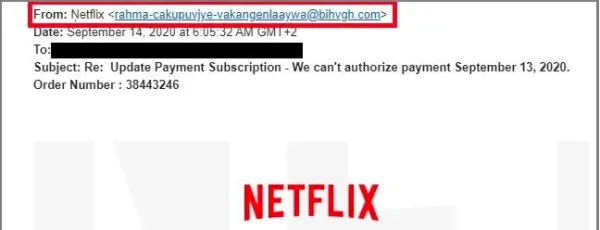
An example of a scam with Netflix, Investopedia
If you spot this red flag, report the email as “Spam” or “Phish.”
2. Poor grammar and spelling
Many scammers are often non-native English speakers or will use automation tools that create language errors.
If you see an email with obvious spelling mistakes, grammatical errors, or awkward sentence structures, that’s a warning sign.Legitimate confirmation digital receipts are well-written, concise, and professional.
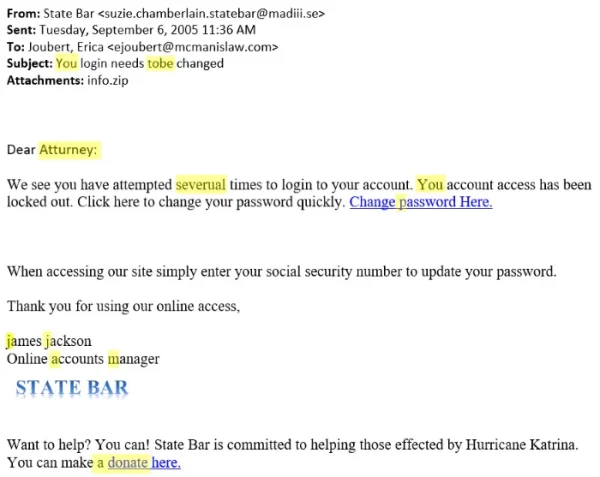
Example of a fake login email with a misspelling, McManisLaw
When you shop online, be vigilant and keep an eye out for emails that seem like they’re from familiar retailers. If there are misspellings, it may be a phishing scam. If there are misspellings, it may be a phishing scam. Additionally, regularly check DMARC reports for your email accounts to enhance your online shopping security.
Don’t forget to verify the sender and cross-check the email addresses and URLs with the official company.
3. Urgency and threats
If an email claims that you don’t have much time to respond or need to take immediate action, then it’s likely a phishing email scam.
The urgency can involve issues with your account, pending transactions, problems with purchases, or legal action that must be taken quickly.
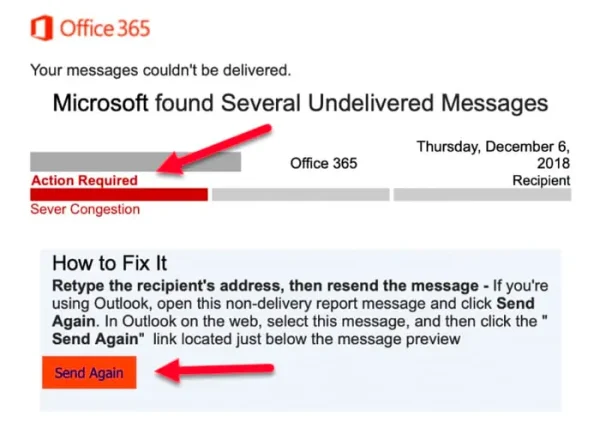
Urgency and suspicious links in an email, GoPTG
Scammers rely on fear and rushed decisions to exploit people, so to protect yourself, proceed with caution when you receive one of these emails.
4. Request for personal information
Scammers often pose as reputable companies and ask recipients to provide sensitive information such as social security numbers, credit card information, and passwords.
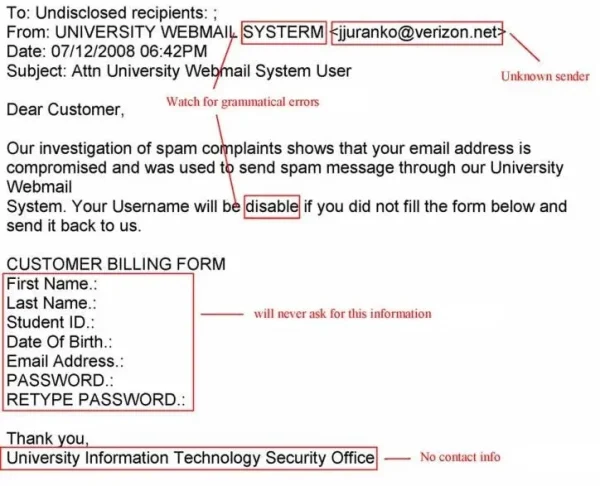
Phishing attempt email scam trying to get your personal information, Chaminade University of Honolulu
Legitimate companies never ask for personal information via email as they prioritize customer security.
If you receive an email asking you to disclose your private information, don’t respond and report it.
5. Unusual attachments or links
Scammers add attachments, links, and buttons such as “view or manage order” buttons to send malicious software to your device.
Clicking on these links could compromise your device’s security or lead to unauthorized access to your personal information.
Rarely will legitimate companies send attachments or have you click on unfamiliar links.
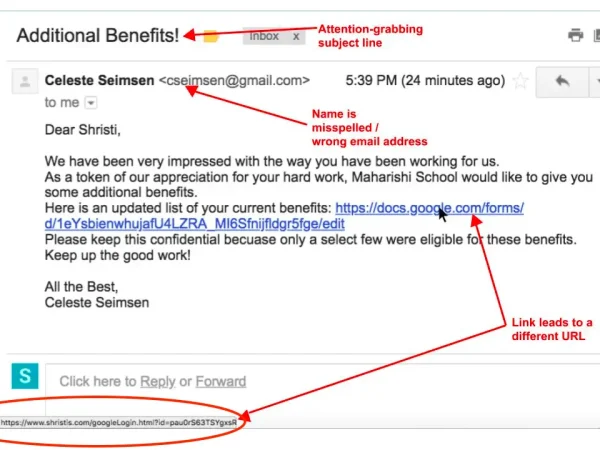
Hover over the link to see where it will take you. Unusual links lead to a different URL. Maharishi School
Avoid opening attachments or clicking on links in confirmation emails if it looks suspicious.
Instead, open a new tab and go directly to the website to check for unauthorized orders.
What tools can you use to avoid spam and phishing?
If you’re worried about falling victim to phishing emails, there are tools and software you can use to avoid being scammed.
1. Create email spam filters
As an extra layer of protection, most email providers allow users to create email filter rules to flag suspicious emails.
Creating email filters on Gmail, dottotech2. Use two-factor authentication (2FA)
Using 2FA helps to protect your information by requiring a second form of verification.
Two-factor authentication is usually a code sent to another device and entering your password again.
A 2FA reduces the risk of unauthorized access to ensure that you’re the only one with the information to log in and access your data.
3. Download software
There are helpful antivirus and anti-malware software that you can use to protect your device, such as McAfee Antivirus Plus, Malwarebytes, and Norton 360 Antivirus With LifeLock.
This software can detect and block malicious viruses in spam and phishing emails.
Frequently asked questions
What is the difference between spam and phishing?
Spam emails are generally unwanted messages that individuals or companies send to your inbox. Usually, they’re trying to sell you a product, service, or newsletter you don’t need or aren’t interested in. Spam mail can get annoying and clutter your inbox. On the other hand, phishing is when someone impersonates another person or a company to steal your sensitive information. Phishing emails can result in malware, identity theft, and financial loss.
Why am I getting spam confirmation emails?
Spammers will often send out mass emails to random addresses, hoping that some of the emails will be opened. The fake email can then reroute you to a spoof login information page.
In closing
Watch out for these red flags of confirmation receipt emails when shopping online.
Report any of these email messages as “spam” and “phish” so that your email provider can build a strong spam filter.
Tammy Dang is a staff writer for Shoeboxed covering productivity, organization, and digitization how-to guides for the home and office. Her favorite organization tip is “1-in-1-out.” And her favorite app for managing writers and deadlines is Monday.com.
About Shoeboxed!
Shoeboxed is a receipt scanning service with receipt management software that supports multiple methods for receipt capture: send, scan, upload, forward, and more!
You can stuff your receipts into one of our Magic Envelopes (prepaid postage within the US). Use our receipt tracker + receipt scanner app (iPhone, iPad and Android) to snap a picture while on the go. Auto-import receipts from Gmail. Or forward a receipt to your designated Shoeboxed email address.
Turn your receipts into data and deductibles with our expense reports that include IRS-accepted receipt images.
Join over 1 million businesses scanning & organizing receipts, creating expense reports and more—with Shoeboxed.
Try Shoeboxed today!



